Data Channel Cryptography Module. More...
#include "crypto_backend.h"#include "basic.h"#include "buffer.h"#include "packet_id.h"#include "mtu.h"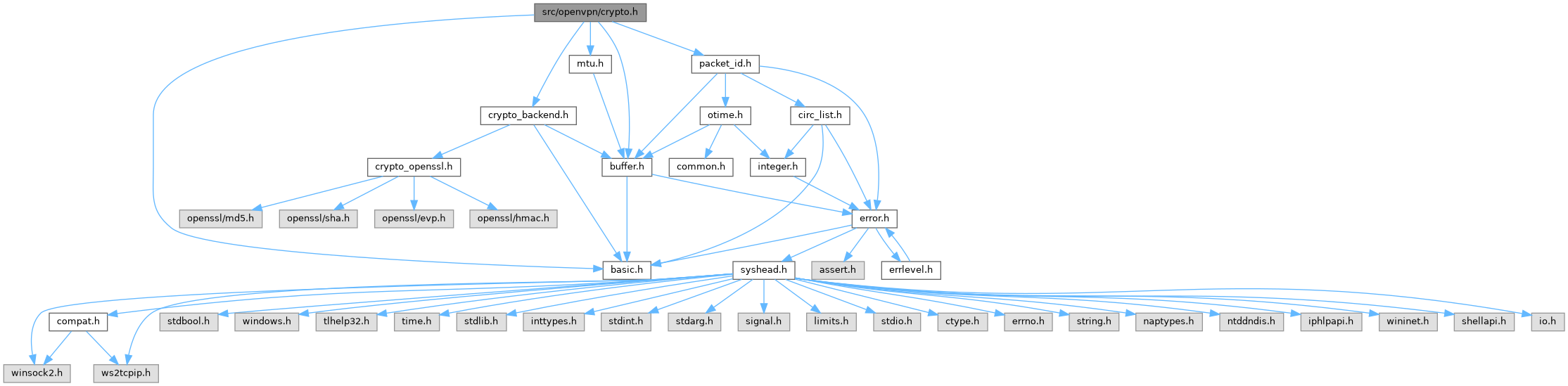
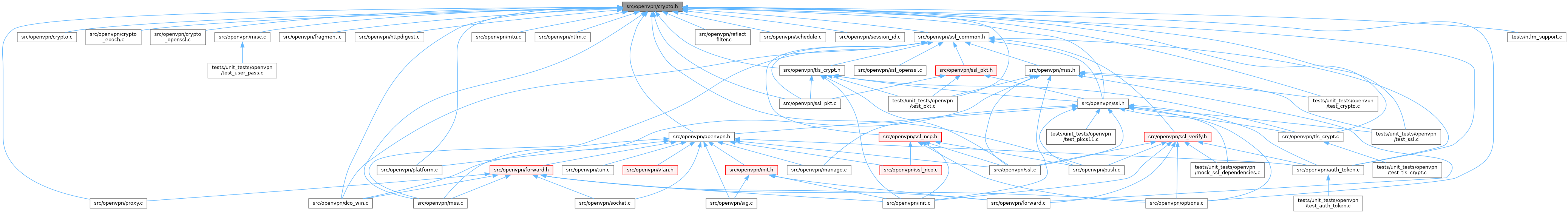
Go to the source code of this file.
Data Structures | |
| struct | sha256_digest |
| Wrapper struct to pass around SHA256 digests. More... | |
| struct | key_type |
| struct | key |
| Container for unidirectional cipher and HMAC key material. More... | |
| struct | key_parameters |
| internal structure similar to struct key that holds key information but is not represented on wire and can be changed/extended More... | |
| struct | epoch_key |
| struct | key_ctx |
| Container for one set of cipher and/or HMAC contexts. More... | |
| struct | key2 |
| Container for bidirectional cipher and HMAC key material. More... | |
| struct | key_direction_state |
Key ordering of the key2.keys array. More... | |
| struct | key_ctx_bi |
| Container for two sets of OpenSSL cipher and/or HMAC contexts for both sending and receiving directions. More... | |
| struct | crypto_options |
| Security parameter state for processing data channel packets. More... | |
Macros | |
| #define | KEY_DIRECTION_BIDIRECTIONAL 0 /* same keys for both directions */ |
| #define | KEY_DIRECTION_NORMAL 1 /* encrypt with keys[0], decrypt with keys[1] */ |
| #define | KEY_DIRECTION_INVERSE 2 /* encrypt with keys[1], decrypt with keys[0] */ |
| #define | CO_PACKET_ID_LONG_FORM (1u << 0) |
| Bit-flag indicating whether to use OpenVPN's long packet ID format. | |
| #define | CO_IGNORE_PACKET_ID (1u << 1) |
| Bit-flag indicating whether to ignore the packet ID of a received packet. | |
| #define | CO_MUTE_REPLAY_WARNINGS (1u << 2) |
| Bit-flag indicating not to display replay warnings. | |
| #define | CO_USE_TLS_KEY_MATERIAL_EXPORT (1u << 3) |
| Bit-flag indicating that data channel key derivation is done using TLS keying material export [RFC5705]. | |
| #define | CO_RESEND_WKC (1u << 4) |
| Bit-flag indicating that the client is expected to resend the wrapped client key with the 2nd packet (packet-id 1) like with the HARD_RESET_CLIENT_V3 packet. | |
| #define | CO_FORCE_TLSCRYPTV2_COOKIE (1u << 5) |
| Bit-flag indicating that we do not allow clients that do not support resending the wrapped client key (WKc) with the third packet of the three-way handshake. | |
| #define | CO_USE_CC_EXIT_NOTIFY (1u << 6) |
| Bit-flag indicating that explicit exit notifies should be sent via the control channel instead of using an OCC message. | |
| #define | CO_USE_DYNAMIC_TLS_CRYPT (1u << 7) |
| Bit-flag indicating that renegotiations are using tls-crypt with a TLS-EKM derived key. | |
| #define | CO_EPOCH_DATA_KEY_FORMAT (1u << 8) |
| Bit-flag indicating the epoch the data format. | |
| #define | CRYPT_ERROR_EXIT(flags, format) |
| #define | CRYPT_ERROR(format) CRYPT_ERROR_EXIT(D_CRYPT_ERRORS, format) |
| #define | CRYPT_DROP(format) CRYPT_ERROR_EXIT(D_MULTI_DROPPED, format) |
| #define | OPENVPN_AEAD_MIN_IV_LEN (sizeof(packet_id_type) + 8) |
| Minimal IV length for AEAD mode ciphers (in bytes): 4-byte packet id + 8 bytes implicit IV. | |
| #define | RKF_MUST_SUCCEED (1 << 0) |
| #define | RKF_INLINE (1 << 1) |
| #define | AEAD_LIMIT_BLOCKSIZE 16 |
| Blocksize used for the AEAD limit caluclation. | |
Functions | |
| void | key_parameters_from_key (struct key_parameters *key_params, const struct key *key) |
| Converts a struct key representation into a struct key_parameters representation. | |
| void | read_key_file (struct key2 *key2, const char *file, const unsigned int flags) |
| int | write_key_file (const int nkeys, const char *filename) |
| Write nkeys 1024-bits keys to file. | |
| bool | check_key (struct key *key, const struct key_type *kt) |
| void | init_key_type (struct key_type *kt, const char *ciphername, const char *authname, bool tls_mode, bool warn) |
| Initialize a key_type structure with. | |
| void | init_key_ctx (struct key_ctx *ctx, const struct key_parameters *key, const struct key_type *kt, int enc, const char *prefix) |
| void | init_key_bi_ctx_send (struct key_ctx *ctx, const struct key_parameters *key, const struct key_type *kt, const char *name) |
| void | init_key_bi_ctx_recv (struct key_ctx *ctx, const struct key_parameters *key, const struct key_type *kt, const char *name) |
| void | free_key_ctx (struct key_ctx *ctx) |
| void | init_key_ctx_bi (struct key_ctx_bi *ctx, const struct key2 *key2, int key_direction, const struct key_type *kt, const char *name) |
| void | free_key_ctx_bi (struct key_ctx_bi *ctx) |
| bool | crypto_check_replay (struct crypto_options *opt, const struct packet_id_net *pin, uint16_t epoch, const char *error_prefix, struct gc_arena *gc) |
| Check packet ID for replay, and perform replay administration. | |
| unsigned int | calculate_crypto_overhead (const struct key_type *kt, unsigned int pkt_id_size, bool occ) |
| Calculate the maximum overhead that our encryption has on a packet. | |
| unsigned int | crypto_max_overhead (void) |
| Return the worst-case OpenVPN crypto overhead (in bytes) | |
| void | write_pem_key_file (const char *filename, const char *key_name) |
| Generate a server key with enough randomness to fill a key struct and write to file. | |
| bool | generate_ephemeral_key (struct buffer *key, const char *pem_name) |
| Generate ephermal key material into the key structure. | |
| bool | read_pem_key_file (struct buffer *key, const char *pem_name, const char *key_file, bool key_inline) |
| Read key material from a PEM encoded files into the key structure. | |
| void | prng_bytes (uint8_t *output, int len) |
| long int | get_random (void) |
| void | print_cipher (const char *cipher) |
| Print a cipher list entry. | |
| void | test_crypto (struct crypto_options *co, struct frame *f) |
| void | key_direction_state_init (struct key_direction_state *kds, int key_direction) |
| void | verify_fix_key2 (struct key2 *key2, const struct key_type *kt, const char *shared_secret_file) |
| void | must_have_n_keys (const char *filename, const char *option, const struct key2 *key2, int n) |
| int | ascii2keydirection (msglvl_t msglevel, const char *str) |
| const char * | keydirection2ascii (int kd, bool remote, bool humanreadable) |
| void | key2_print (const struct key2 *k, const struct key_type *kt, const char *prefix0, const char *prefix1) |
| Prints the keys in a key2 structure. | |
| void | crypto_read_openvpn_key (const struct key_type *key_type, struct key_ctx_bi *ctx, const char *key_file, bool key_inline, const int key_direction, const char *key_name, const char *opt_name, struct key2 *keydata) |
| void | generate_test_crypto_random_key (const struct key_type *key_type, struct key_ctx_bi *ctx, const char *key_name) |
| Generate a random key and initialise ctx to be used the in the crypto random test. | |
| int | memcmp_constant_time (const void *a, const void *b, size_t size) |
| As memcmp(), but constant-time. | |
| static bool | key_ctx_bi_defined (const struct key_ctx_bi *key) |
| const char * | print_key_filename (const char *str, bool is_inline) |
| To be used when printing a string that may contain inline data. | |
| static struct key_type | create_kt (const char *cipher, const char *md, const char *optname) |
| Creates and validates an instance of struct key_type with the provided algs. | |
| uint64_t | cipher_get_aead_limits (const char *ciphername) |
| Check if the cipher is an AEAD cipher and needs to be limited to a certain number of number of blocks + packets. | |
| static bool | cipher_decrypt_verify_fail_exceeded (const struct key_ctx *ctx) |
| Check if the number of failed decryption is over the acceptable limit. | |
| static bool | cipher_decrypt_verify_fail_warn (const struct key_ctx *ctx) |
| Check if the number of failed decryption is approaching the limit and we should try to move to a new key. | |
| bool | check_tls_prf_working (void) |
| Checks if the current TLS library supports the TLS 1.0 PRF with MD5+SHA1 that OpenVPN uses when TLS Keying Material Export is not available. | |
| static bool | aead_usage_limit_reached (const uint64_t limit, const struct key_ctx *key_ctx, int64_t higest_pid) |
| Checks if the usage limit for an AEAD cipher is reached. | |
Functions for performing security operations on data channel packets | |
| void | openvpn_encrypt (struct buffer *buf, struct buffer work, struct crypto_options *opt) |
| Encrypt and HMAC sign a packet so that it can be sent as a data channel VPN tunnel packet to a remote OpenVPN peer. | |
| bool | openvpn_decrypt (struct buffer *buf, struct buffer work, struct crypto_options *opt, const struct frame *frame, const uint8_t *ad_start) |
| HMAC verify and decrypt a data channel packet received from a remote OpenVPN peer. | |
Detailed Description
Data Channel Cryptography Module.
Definition in file crypto.h.
Macro Definition Documentation
◆ AEAD_LIMIT_BLOCKSIZE
| #define AEAD_LIMIT_BLOCKSIZE 16 |
Blocksize used for the AEAD limit caluclation.
Since cipher_ctx_block_size() is not reliable and will return 1 in many cases use a hardcoded blocksize instead
◆ CO_EPOCH_DATA_KEY_FORMAT
| #define CO_EPOCH_DATA_KEY_FORMAT (1u << 8) |
◆ CO_FORCE_TLSCRYPTV2_COOKIE
| #define CO_FORCE_TLSCRYPTV2_COOKIE (1u << 5) |
◆ CO_IGNORE_PACKET_ID
| #define CO_IGNORE_PACKET_ID (1u << 1) |
◆ CO_MUTE_REPLAY_WARNINGS
| #define CO_MUTE_REPLAY_WARNINGS (1u << 2) |
◆ CO_PACKET_ID_LONG_FORM
| #define CO_PACKET_ID_LONG_FORM (1u << 0) |
◆ CO_RESEND_WKC
| #define CO_RESEND_WKC (1u << 4) |
◆ CO_USE_CC_EXIT_NOTIFY
| #define CO_USE_CC_EXIT_NOTIFY (1u << 6) |
◆ CO_USE_DYNAMIC_TLS_CRYPT
| #define CO_USE_DYNAMIC_TLS_CRYPT (1u << 7) |
◆ CO_USE_TLS_KEY_MATERIAL_EXPORT
| #define CO_USE_TLS_KEY_MATERIAL_EXPORT (1u << 3) |
◆ CRYPT_DROP
| #define CRYPT_DROP | ( | format | ) | CRYPT_ERROR_EXIT(D_MULTI_DROPPED, format) |
◆ CRYPT_ERROR
| #define CRYPT_ERROR | ( | format | ) | CRYPT_ERROR_EXIT(D_CRYPT_ERRORS, format) |
◆ CRYPT_ERROR_EXIT
| #define CRYPT_ERROR_EXIT | ( | flags, | |
| format | |||
| ) |
◆ KEY_DIRECTION_BIDIRECTIONAL
| #define KEY_DIRECTION_BIDIRECTIONAL 0 /* same keys for both directions */ |
◆ KEY_DIRECTION_INVERSE
| #define KEY_DIRECTION_INVERSE 2 /* encrypt with keys[1], decrypt with keys[0] */ |
◆ KEY_DIRECTION_NORMAL
| #define KEY_DIRECTION_NORMAL 1 /* encrypt with keys[0], decrypt with keys[1] */ |
◆ OPENVPN_AEAD_MIN_IV_LEN
| #define OPENVPN_AEAD_MIN_IV_LEN (sizeof(packet_id_type) + 8) |
◆ RKF_INLINE
◆ RKF_MUST_SUCCEED
Function Documentation
◆ aead_usage_limit_reached()
|
inlinestatic |
Checks if the usage limit for an AEAD cipher is reached.
This method abstracts the calculation to make the calling function easier to read.
Definition at line 760 of file crypto.h.
References key_ctx::plaintext_blocks.
Referenced by check_aead_limits(), epoch_check_send_iterate(), and should_trigger_renegotiation().
◆ ascii2keydirection()
| int ascii2keydirection | ( | msglvl_t | msglevel, |
| const char * | str | ||
| ) |
Definition at line 1641 of file crypto.c.
References KEY_DIRECTION_BIDIRECTIONAL, KEY_DIRECTION_INVERSE, KEY_DIRECTION_NORMAL, and msg.
Referenced by add_option().
◆ calculate_crypto_overhead()
| unsigned int calculate_crypto_overhead | ( | const struct key_type * | kt, |
| unsigned int | pkt_id_size, | ||
| bool | occ | ||
| ) |
Calculate the maximum overhead that our encryption has on a packet.
This does not include needed additional buffer size
This does NOT include the padding and rounding of CBC size as the users (mssfix/fragment) of this function need to adjust for this and add it themselves.
- Parameters
-
kt Struct with the crypto algorithm to use pkt_id_size Size of the packet id occ if true calculates the overhead for crypto in the same incorrect way as all previous OpenVPN versions did, to end up with identical numbers for OCC compatibility
Definition at line 808 of file crypto.c.
References key_type::cipher, cipher_defined(), cipher_kt_block_size(), cipher_kt_iv_size(), cipher_kt_mode_aead(), cipher_kt_mode_cbc(), cipher_kt_tag_size(), key_type::digest, buffer::len, md_defined(), and md_kt_size().
Referenced by frame_calculate_protocol_header_size().
◆ check_key()
Definition at line 1131 of file crypto.c.
References key_type::cipher, cipher_defined(), and key_is_zero().
Referenced by generate_key_expansion(), and verify_fix_key2().
◆ check_tls_prf_working()
| bool check_tls_prf_working | ( | void | ) |
Checks if the current TLS library supports the TLS 1.0 PRF with MD5+SHA1 that OpenVPN uses when TLS Keying Material Export is not available.
- Returns
- true if supported, false otherwise.
Definition at line 1924 of file crypto.c.
References ssl_tls1_PRF().
Referenced by options_process_mutate_prf().
◆ cipher_decrypt_verify_fail_exceeded()
|
inlinestatic |
Check if the number of failed decryption is over the acceptable limit.
Definition at line 716 of file crypto.h.
References key_ctx::failed_verifications.
Referenced by openvpn_decrypt_aead().
◆ cipher_decrypt_verify_fail_warn()
|
inlinestatic |
Check if the number of failed decryption is approaching the limit and we should try to move to a new key.
Definition at line 731 of file crypto.h.
References key_ctx::failed_verifications.
Referenced by epoch_check_send_iterate(), and should_trigger_renegotiation().
◆ cipher_get_aead_limits()
| uint64_t cipher_get_aead_limits | ( | const char * | ciphername | ) |
Check if the cipher is an AEAD cipher and needs to be limited to a certain number of number of blocks + packets.
Return 0 if ciphername is not an AEAD cipher or no limit (e.g. Chacha20-Poly1305) is needed. (Or the limit is larger than 2^64)
For reference see the OpenVPN RFC draft and https://www.ietf.org/archive/id/draft-irtf-cfrg-aead-limits-08.html
Definition at line 350 of file crypto.c.
References cipher_kt_mode_aead(), cipher_kt_name(), and buffer::len.
Referenced by crypto_test_aead_limits(), epoch_init_key_ctx(), and tls_get_limit_aead().
◆ create_kt()
|
inlinestatic |
Creates and validates an instance of struct key_type with the provided algs.
- Parameters
-
cipher the cipher algorithm to use (must be a string literal) md the digest algorithm to use (must be a string literal) optname the name of the option requiring the key_type object
- Returns
- the initialized key_type instance
Definition at line 681 of file crypto.h.
References key_type::cipher, cipher_defined(), cipher_valid(), key_type::digest, M_WARN, md_defined(), md_valid(), and msg.
Referenced by auth_token_kt(), init_crypto_options(), and tls_crypt_kt().
◆ crypto_check_replay()
| bool crypto_check_replay | ( | struct crypto_options * | opt, |
| const struct packet_id_net * | pin, | ||
| uint16_t | epoch, | ||
| const char * | error_prefix, | ||
| struct gc_arena * | gc | ||
| ) |
Check packet ID for replay, and perform replay administration.
- Parameters
-
opt Crypto options for this packet, contains replay state. pin Packet ID read from packet. epoch Epoch read from packet or 0 when epoch is not used. error_prefix Prefix to use when printing error messages. gc Garbage collector to use.
- Returns
- true if packet ID is validated to be not a replay, false otherwise.
Definition at line 381 of file crypto.c.
References CO_MUTE_REPLAY_WARNINGS, CO_PACKET_ID_LONG_FORM, D_GENKEY, D_REPLAY_ERRORS, key_ctx_bi::decrypt, key_ctx::epoch, epoch_replace_update_recv_key(), crypto_options::epoch_retiring_data_receive_key, crypto_options::epoch_retiring_key_pid_recv, crypto_options::flags, gc, crypto_options::key_ctx_bi, msg, crypto_options::packet_id, packet_id_add(), packet_id_net_print(), packet_id_persist_save_obj(), packet_id_reap_test(), packet_id_test(), crypto_options::pid_persist, and packet_id::rec.
Referenced by openvpn_decrypt_aead(), openvpn_decrypt_v1(), and tls_crypt_unwrap().
◆ crypto_max_overhead()
| unsigned int crypto_max_overhead | ( | void | ) |
Return the worst-case OpenVPN crypto overhead (in bytes)
Definition at line 855 of file crypto.c.
References max_int(), OPENVPN_AEAD_TAG_LENGTH, OPENVPN_MAX_CIPHER_BLOCK_SIZE, OPENVPN_MAX_HMAC_SIZE, OPENVPN_MAX_IV_LENGTH, and packet_id_size().
Referenced by frame_finalize_options().
◆ crypto_read_openvpn_key()
| void crypto_read_openvpn_key | ( | const struct key_type * | key_type, |
| struct key_ctx_bi * | ctx, | ||
| const char * | key_file, | ||
| bool | key_inline, | ||
| const int | key_direction, | ||
| const char * | key_name, | ||
| const char * | opt_name, | ||
| struct key2 * | keydata | ||
| ) |
Definition at line 1299 of file crypto.c.
References init_key_ctx_bi(), key2, key_direction_state_init(), M_ERR, msg, must_have_n_keys(), key2::n, key_direction_state::need_keys, print_key_filename(), read_key_file(), RKF_INLINE, RKF_MUST_SUCCEED, secure_memzero(), and verify_fix_key2().
Referenced by do_init_crypto_static(), do_init_tls_wrap_key(), init_tas_auth(), and tls_crypt_init_key().
◆ free_key_ctx()
| void free_key_ctx | ( | struct key_ctx * | ctx | ) |
Definition at line 1086 of file crypto.c.
References key_ctx::cipher, cipher_ctx_free(), CLEAR, key_ctx::epoch, key_ctx::hmac, hmac_ctx_cleanup(), hmac_ctx_free(), key_ctx::implicit_iv, and key_ctx::plaintext_blocks.
Referenced by auth_token_fail_invalid_key(), auth_token_test_key_load(), auth_token_test_random_keys(), crypto_test_epoch_key_generation(), do_close_free_key_schedule(), epoch_generate_future_receive_keys(), epoch_iterate_send_key(), epoch_replace_update_recv_key(), free_epoch_key_ctx(), free_key_ctx_bi(), key_schedule_free(), teardown(), tls_crypt_fail_invalid_key(), and tls_crypt_v2_write_client_key_file().
◆ free_key_ctx_bi()
| void free_key_ctx_bi | ( | struct key_ctx_bi * | ctx | ) |
Definition at line 1105 of file crypto.c.
References key_ctx_bi::decrypt, key_ctx_bi::encrypt, free_key_ctx(), and key_ctx_bi::initialized.
Referenced by crypto_test_epoch_teardown(), do_close_free_key_schedule(), free_tas(), free_tls_pre_decrypt_state(), key_schedule_free(), key_state_free(), test_tls_crypt_teardown(), test_tls_crypt_v2_teardown(), test_tls_decrypt_lite_auth(), test_tls_decrypt_lite_crypt(), tls_crypt_v2_wrap_unwrap_wrong_key(), tls_crypt_v2_write_client_key_file(), tls_wrap_free(), and uninit_crypto_options().
◆ generate_ephemeral_key()
| bool generate_ephemeral_key | ( | struct buffer * | key, |
| const char * | pem_name | ||
| ) |
Generate ephermal key material into the key structure.
- Parameters
-
key the key structure that will hold the key material pem_name the name used for logging
- Returns
- true if key generation was successful
Definition at line 1869 of file crypto.c.
References BCAP, BEND, buf_inc_len(), buffer::len, M_INFO, M_WARN, msg, and rand_bytes().
Referenced by auth_token_init_secret().
◆ generate_test_crypto_random_key()
| void generate_test_crypto_random_key | ( | const struct key_type * | key_type, |
| struct key_ctx_bi * | ctx, | ||
| const char * | key_name | ||
| ) |
Generate a random key and initialise ctx to be used the in the crypto random test.
Definition at line 1338 of file crypto.c.
References generate_key_random(), init_key_ctx_bi(), KEY_DIRECTION_BIDIRECTIONAL, key2::keys, and key2::n.
Referenced by do_init_crypto_test().
◆ get_random()
| long int get_random | ( | void | ) |
Definition at line 1745 of file crypto.c.
References prng_bytes().
Referenced by check_send_occ_msg_dowork(), check_timeout_random_component_dowork(), do_init_crypto_tls(), fragment_init(), init_connection_list(), multi_init(), packet_id_add(), and platform_create_temp_file().
◆ init_key_bi_ctx_recv()
| void init_key_bi_ctx_recv | ( | struct key_ctx * | ctx, |
| const struct key_parameters * | key, | ||
| const struct key_type * | kt, | ||
| const char * | name | ||
| ) |
Definition at line 1055 of file crypto.c.
References key_parameters::epoch, key_ctx::epoch, init_key_ctx(), key_ctx_update_implicit_iv(), and OPENVPN_OP_DECRYPT.
Referenced by epoch_init_recv_key(), and init_key_ctx_bi().
◆ init_key_bi_ctx_send()
| void init_key_bi_ctx_send | ( | struct key_ctx * | ctx, |
| const struct key_parameters * | key, | ||
| const struct key_type * | kt, | ||
| const char * | name | ||
| ) |
Definition at line 1043 of file crypto.c.
References key_parameters::epoch, key_ctx::epoch, init_key_ctx(), key_ctx_update_implicit_iv(), and OPENVPN_OP_ENCRYPT.
Referenced by epoch_init_send_key_ctx(), and init_key_ctx_bi().
◆ init_key_ctx()
| void init_key_ctx | ( | struct key_ctx * | ctx, |
| const struct key_parameters * | key, | ||
| const struct key_type * | kt, | ||
| int | enc, | ||
| const char * | prefix | ||
| ) |
Definition at line 1001 of file crypto.c.
References ASSERT, key_type::cipher, key::cipher, key_ctx::cipher, cipher_ctx_init(), cipher_ctx_new(), cipher_defined(), cipher_kt_block_size(), cipher_kt_iv_size(), cipher_kt_key_size(), cipher_kt_name(), CLEAR, D_CIPHER_INIT, D_CRYPTO_DEBUG, D_SHOW_KEYS, key_type::digest, dmsg, key_ctx::epoch, format_hex(), gc, gc_free(), gc_new(), key::hmac, key_ctx::hmac, hmac_ctx_init(), hmac_ctx_new(), hmac_ctx_size(), md_defined(), md_kt_name(), md_kt_size(), msg, and warn_insecure_key_type().
Referenced by auth_token_fail_invalid_key(), auth_token_init_secret(), init_key_bi_ctx_recv(), init_key_bi_ctx_send(), setup(), test_tls_crypt_setup(), tls_crypt_fail_invalid_key(), and tls_crypt_v2_init_server_key().
◆ init_key_ctx_bi()
| void init_key_ctx_bi | ( | struct key_ctx_bi * | ctx, |
| const struct key2 * | key2, | ||
| int | key_direction, | ||
| const struct key_type * | kt, | ||
| const char * | name | ||
| ) |
Definition at line 1067 of file crypto.c.
References key_ctx_bi::decrypt, key_ctx_bi::encrypt, key_direction_state::in_key, init_key_bi_ctx_recv(), init_key_bi_ctx_send(), key_ctx_bi::initialized, key_direction_state_init(), key_parameters_from_key(), key2::keys, and key_direction_state::out_key.
Referenced by crypto_read_openvpn_key(), generate_test_crypto_random_key(), init_crypto_options(), init_key_contexts(), test_tls_crypt_v2_setup(), tls_crypt_v2_load_client_key(), tls_crypt_v2_wrap_unwrap_wrong_key(), and tls_session_generate_dynamic_tls_crypt_key().
◆ init_key_type()
| void init_key_type | ( | struct key_type * | kt, |
| const char * | ciphername, | ||
| const char * | authname, | ||
| bool | tls_mode, | ||
| bool | warn | ||
| ) |
Initialize a key_type structure with.
- Parameters
-
kt The struct key_type to initialize ciphername The name of the cipher to use authname The name of the HMAC digest to use tls_mode Specifies whether we are running in TLS mode, which allows more ciphers than static key mode. warn Print warnings when null cipher / auth is used.
Definition at line 880 of file crypto.c.
References ASSERT, key_type::cipher, cipher_kt_block_size(), cipher_kt_mode_aead(), cipher_kt_mode_cbc(), cipher_kt_mode_ofb_cfb(), cipher_valid(), CLEAR, key_type::digest, buffer::len, M_FATAL, M_WARN, md_kt_size(), msg, OPENVPN_MAX_CIPHER_BLOCK_SIZE, OPENVPN_MAX_HMAC_SIZE, and warn_insecure_key_type().
Referenced by calc_options_string_link_mtu(), crypto_test_epoch_setup(), do_init_crypto_none(), do_init_crypto_static(), do_init_crypto_test(), do_init_crypto_tls_c1(), epoch_test_derive_data_key(), init_tas_auth(), options_string(), test_mssfix_mtu_calculation(), and tls_session_update_crypto_params_do_work().
◆ key2_print()
| void key2_print | ( | const struct key2 * | k, |
| const struct key_type * | kt, | ||
| const char * | prefix0, | ||
| const char * | prefix1 | ||
| ) |
Prints the keys in a key2 structure.
Definition at line 1185 of file crypto.c.
References ASSERT, key_print(), key2::keys, and key2::n.
Referenced by generate_key_expansion().
◆ key_ctx_bi_defined()
|
inlinestatic |
Definition at line 653 of file crypto.h.
References key::cipher, and key::hmac.
Referenced by do_init_crypto_static(), and do_init_crypto_test().
◆ key_direction_state_init()
| void key_direction_state_init | ( | struct key_direction_state * | kds, |
| int | key_direction | ||
| ) |
Definition at line 1693 of file crypto.c.
References ASSERT, CLEAR, key_direction_state::in_key, KEY_DIRECTION_BIDIRECTIONAL, KEY_DIRECTION_INVERSE, KEY_DIRECTION_NORMAL, key_direction_state::need_keys, and key_direction_state::out_key.
Referenced by crypto_read_openvpn_key(), init_epoch_keys(), init_key_ctx_bi(), and tls_session_generate_dynamic_tls_crypt_key().
◆ key_parameters_from_key()
| void key_parameters_from_key | ( | struct key_parameters * | key_params, |
| const struct key * | key | ||
| ) |
Converts a struct key representation into a struct key_parameters representation.
- Parameters
-
key_params destination for the converted struct key source of the conversion
Definition at line 1194 of file crypto.c.
References key::cipher, key_parameters::cipher, key_parameters::cipher_size, CLEAR, key::hmac, key_parameters::hmac, key_parameters::hmac_size, MAX_CIPHER_KEY_LENGTH, and MAX_HMAC_KEY_LENGTH.
Referenced by auth_token_init_secret(), init_key_ctx_bi(), and tls_crypt_v2_init_server_key().
◆ keydirection2ascii()
| const char * keydirection2ascii | ( | int | kd, |
| bool | remote, | ||
| bool | humanreadable | ||
| ) |
Definition at line 1664 of file crypto.c.
References ASSERT, KEY_DIRECTION_BIDIRECTIONAL, KEY_DIRECTION_INVERSE, and KEY_DIRECTION_NORMAL.
Referenced by options_string(), show_connection_entry(), and show_settings().
◆ memcmp_constant_time()
| int memcmp_constant_time | ( | const void * | a, |
| const void * | b, | ||
| size_t | size | ||
| ) |
As memcmp(), but constant-time.
Returns 0 when data is equal, non-zero otherwise.
Definition at line 1355 of file crypto_openssl.c.
Referenced by check_hmac_token(), check_session_hmac_and_pkt_id(), is_auth_token(), man_check_password(), openvpn_decrypt_v1(), tls_crypt_unwrap(), tls_crypt_v2_unwrap_client_key(), verify_auth_token(), and verify_cert().
◆ must_have_n_keys()
| void must_have_n_keys | ( | const char * | filename, |
| const char * | option, | ||
| const struct key2 * | key2, | ||
| int | n | ||
| ) |
◆ print_cipher()
| void print_cipher | ( | const char * | cipher | ) |
Print a cipher list entry.
Definition at line 1757 of file crypto.c.
References cipher_kt_block_size(), cipher_kt_key_size(), cipher_kt_mode_cbc(), cipher_kt_name(), and cipher_valid_reason().
Referenced by show_available_ciphers().
◆ print_key_filename()
| const char * print_key_filename | ( | const char * | str, |
| bool | is_inline | ||
| ) |
To be used when printing a string that may contain inline data.
If "is_inline" is true, return the inline tag. If "is_inline" is false and "str" is not NULL, return "str". Return the constant string "[NULL]" otherwise.
- Parameters
-
str the original string to return when is_inline is false is_inline true when str contains an inline data of some sort
Definition at line 1288 of file crypto.c.
References buffer::len, and np().
Referenced by backend_tls_ctx_reload_crl(), crypto_read_openvpn_key(), read_key_file(), tls_ctx_load_ca(), tls_ctx_load_dh_params(), tls_ctx_load_extra_certs(), and tls_ctx_load_priv_file().
◆ prng_bytes()
| void prng_bytes | ( | uint8_t * | output, |
| int | len | ||
| ) |
Definition at line 1738 of file crypto.c.
References ASSERT, and rand_bytes().
Referenced by get_random(), hostname_randomize(), openvpn_encrypt_v1(), and session_id_random().
◆ read_key_file()
| void read_key_file | ( | struct key2 * | key2, |
| const char * | file, | ||
| const unsigned int | flags | ||
| ) |
Definition at line 1362 of file crypto.c.
References ASSERT, buf_clear(), buf_set_read(), buf_valid(), buffer_read_from_file(), CLEAR, buffer::data, format_hex_ex(), gc, gc_free(), gc_new(), key2::keys, buffer::len, M_FATAL, M_INFO, msg, key2::n, PARSE_DATA, PARSE_DATA_COMPLETE, PARSE_FINISHED, PARSE_FOOT, PARSE_HEAD, PARSE_INITIAL, print_key_filename(), printable_char_fmt, RKF_INLINE, RKF_MUST_SUCCEED, SIZE, static_key_foot, static_key_head, and unprintable_char_fmt.
Referenced by crypto_read_openvpn_key().
◆ read_pem_key_file()
| bool read_pem_key_file | ( | struct buffer * | key, |
| const char * | pem_name, | ||
| const char * | key_file, | ||
| bool | key_inline | ||
| ) |
Read key material from a PEM encoded files into the key structure.
- Parameters
-
key the key structure that will hold the key material pem_name the name used in the pem encoding start/end lines key_file name of the file to read or the key itself if key_inline is true key_inline True if key_file contains an inline key, False otherwise.
- Returns
- true if reading into key was successful
Definition at line 1887 of file crypto.c.
References buf_clear(), buf_set_read(), buf_valid(), buffer_read_from_file(), cleanup(), crypto_pem_decode(), gc, gc_free(), gc_new(), buffer::len, M_WARN, and msg.
Referenced by auth_token_init_secret(), tls_crypt_v2_init_client_key(), and tls_crypt_v2_init_server_key().
◆ test_crypto()
| void test_crypto | ( | struct crypto_options * | co, |
| struct frame * | f | ||
| ) |
Definition at line 1204 of file crypto.c.
References alloc_buf_gc(), ASSERT, BLEN, BLENZ, BPTR, frame::buf, buf_init, BUF_SIZE, buf_write_alloc(), key_ctx::cipher, cipher_ctx_iv_length(), cipher_ctx_mode_aead(), clear_buf(), key_ctx_bi::decrypt, key_ctx_bi::encrypt, gc, gc_free(), gc_new(), frame::headroom, key_ctx::implicit_iv, crypto_options::key_ctx_bi, buffer::len, M_FATAL, M_INFO, msg, OPENVPN_AEAD_MIN_IV_LEN, openvpn_decrypt(), openvpn_encrypt(), OPENVPN_MAX_IV_LENGTH, frame::payload_size, rand_bytes(), and update_time().
Referenced by do_test_crypto(), and show_settings().
◆ verify_fix_key2()
| void verify_fix_key2 | ( | struct key2 * | key2, |
| const struct key_type * | kt, | ||
| const char * | shared_secret_file | ||
| ) |
Definition at line 1722 of file crypto.c.
References check_key(), key2::keys, M_FATAL, msg, and key2::n.
Referenced by crypto_read_openvpn_key().
◆ write_key_file()
| int write_key_file | ( | const int | nkeys, |
| const char * | filename | ||
| ) |
Write nkeys 1024-bits keys to file.
- Returns
- number of random bits written, or -1 on failure.
Definition at line 1565 of file crypto.c.
References alloc_buf_gc(), BLEN, BPTR, buf_clear(), buf_printf(), buffer_write_file(), format_hex_ex(), gc, gc_free(), gc_new(), generate_key_random(), buffer::len, secure_memzero(), static_key_foot, and static_key_head.
Referenced by do_genkey().
◆ write_pem_key_file()
| void write_pem_key_file | ( | const char * | filename, |
| const char * | key_name | ||
| ) |
Generate a server key with enough randomness to fill a key struct and write to file.
- Parameters
-
filename Filename of the server key file to create. key_name The name to use in the PEM header/footer.
Definition at line 1832 of file crypto.c.
References BLEN, BPTR, buf_clear(), buf_set_read(), buffer_write_file(), cleanup(), clear_buf(), crypto_pem_encode(), gc, gc_free(), gc_new(), buffer::len, M_ERR, M_NONFATAL, M_WARN, msg, rand_bytes(), and secure_memzero().
Referenced by auth_token_write_server_key_file(), and tls_crypt_v2_write_server_key_file().